WordPress plugins hacked
On Monday, June 24, 2024, Wordfence noticed a backdoor attack with several WordPress plugins hacked. They found malware in updates for the plugins that were available from the official WordPress website.
The malware automatically creates a user with admin rights, giving the hackers full control of the site. There have also been cases of malicious JavaScript code in the footer filling the site with spam content.
For those of you who are concerned, below is a list on the affected plugins and how to easily check if your concerns are justified.
5 infected plugins
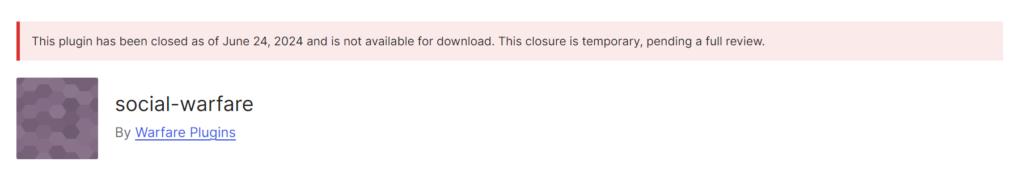
Five plugins, which together have over 36 000 downloads, have been identified as compromised. To prevent further breaches, they have been temporarily suspended.
Please check if you have any of these installed on your site:
- Social Warfare: versions 4.4.6.4 – 4.4.7.1 (fixed in 4.4.7.3)
- BLAZE Retail Widget: versions 2.2.5 – 2.5.2 (fixed in 2.5.4)
- Wrapper Link Elementor: versions 1.0.2 – 1.0.3 (fixed in 1.0.5)
- Contact Form 7 Multi-Step Addon: versions 1.0.4 – 1.0.5 (fixed in 1.0.7)
- Simply Show Hooks: versions 1.2.1 – 1.2.2 (not fixed at this time)
What can I do?
As a customer, you’re always welcome to contact our support during opening hours. In this case, however, there’s some quick and easy ways to check if you’re affected by the breach.
Here are three things to look out for:
- Check your plugins: Start by checking if you have any of the above plugins installed on your site.
- Double check your users: Go to your admin panel and click on Users in the left-hand menu. Inspect your users: Is there any user named “wpcron<SIGNSANDNUMBERSHERE>“? The length of the digits may vary, but the user always seems to be registered 1979-01-01.
- Consult our security program: Enter cPanel and go to Imunify. Under the History tab, you can see if you have had any recent hits. If you see files from the “.cagefs/tmp” folder, it’s a sign that you’ve been hit by the current wave. Check if you get any hits at all from the last week. See which file was flagged as infected in the last week, investigate it further and if needed, contact our support for help interpreting why the file was flagged by Imunify.
If you think a user is someone who shouldn’t have access to your site (wpcron in the name, weird domain addresses, etc), it’s better to remove them and later on adding them back if they were in fact someone sho should’ve had access. Adding new users takes minutes, while clearing malware can take days.
What we are doing
Our clients who are using Managed WordPress, where we update, optimize and monitor your site, and have been infected have already been contacted by us. We are currently working on clearing these accounts.
We will continue to scan our servers for suspicious users and will contact you via your customer account if we find anything.
What’s a “backdoor”?
A backdoor is a way to get into a system without having to log in. It’s a type of virus that aims to give the hacker access to your systems without going through the normal security measures. In this case, the hackers have used existing WordPress plugins as the “backdoor” to get in.
You can catch a backdoor birus in a number of ways, including through phishing or by it posing as a legitimate program, a so-called Trojan.
And how does it work in a supply chain attack?
A supply chain attack is a way to access sensitive information via a trusted source. This way, the victim is less likely to be alert to what’s happening.
It could be, as in the current case, that the attackers are targeting a plugin. When the malware has been added, they send out an update to you and anyone else using the program (or plugin). When you see that there’s an update, you don’t think anything strange. And why would you? You trust the source. After all, it’s worked perfectly before and it’s usually safe. Et voilá – the hackers have gained access to your systems. Hacked WordPress plugins then need to be cleaned up.
So the target is not necessarily the initially hacked provider, but their customers. An effective ploy, as it allows them to attack more people with less effort.